Cybersecurity Monitoring Services
Security, Visibility, Detection
We ensure the operational integrity, security and performance of a client’s Azure Cloud environments, proactively detecting and preventing cybersecurity incidents and suspicious activity. Our centralized Azure cybersecurity monitoring services allow clients to reduce risk and improve compliance, through:
- Artificial intelligence & machine learning automation;
- Continuous process improvement;
- Reusable components & templates;
- Workflow automation; and
- Integrated Azure SecOps.
Clients get increased visibility into and stronger control over, the security of their Azure cloud resources. This includes detail around critical security events, threats, vulnerabilities, and top offenders.

Expand Your Security Visibility with Azure Cybersecurity Monitoring
For more than two decades, our experienced security engineers have outlined and implemented specific, actionable steps to improve cybersecurity for companies across multiple industries. Those industries include financial services, global media, healthcare, education, retail and technology.
Our suite of essential Azure cybersecurity monitoring services, overseen by our Azure security experts in real-time at our state-of-the-art Security Operations Center, include:
The Neovera Shared Security Model
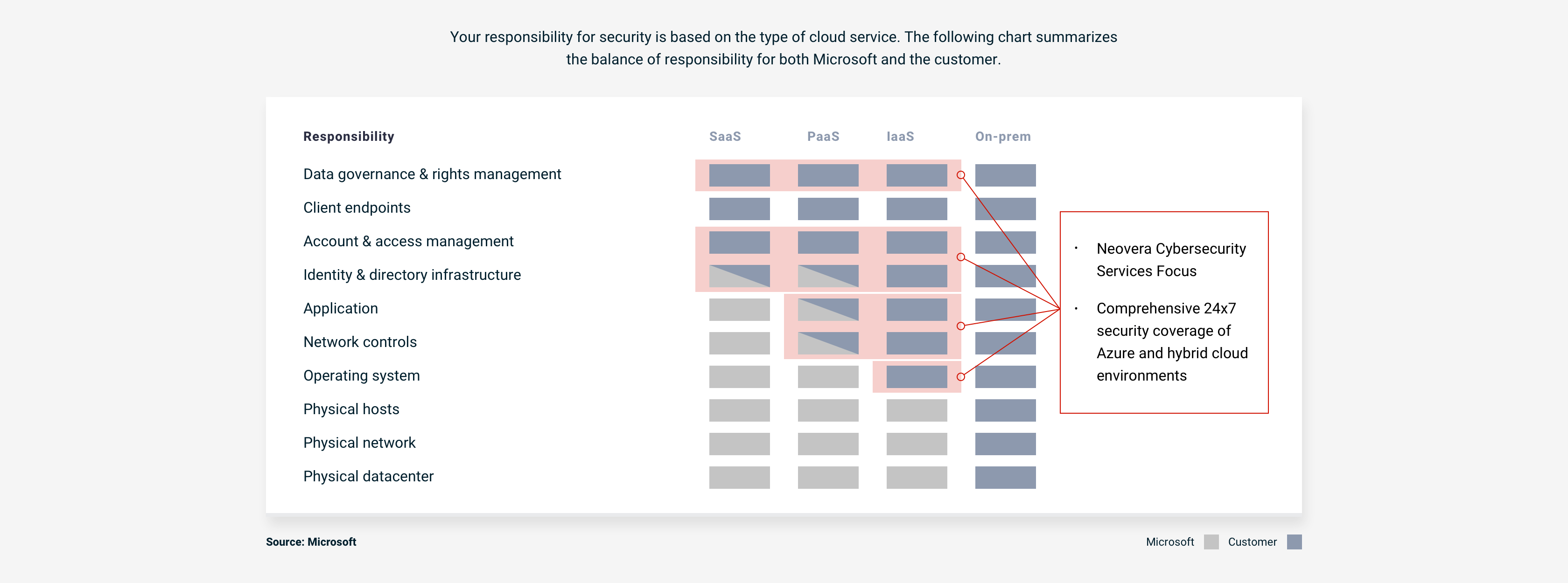
Managing and maintaining your Cloud security is a lot to be responsible for, on top of running your business. How can you be sure you’re keeping your Cloud, and your data, 100 percent safe and secure? Or would you want your Cloud service provider to have complete control over everything? Probably not.
Cloud security is only effective when there is a realistic division of responsibilities. The chart explains the Neovera shared security model in different Cloud environments. Clients are responsible for the dark gray areas, while the light gray areas fall to Microsoft. With our comprehensive 24×7 security coverage of critical areas in Azure and hybrid Clouds, including data governance and rights management and account and access management, you can focus on your operations and your clients.
We Simplify Your Cybersecurity Operations; You Keep Control
No matter the Cloud you choose—IaaS, PaaS, or SaaS—you retain direct control over your data as well as the application logic and code, identity and access, and platform and resource configuration. You also manage everything connecting you to the Cloud, including on-premises infrastructure stack and user devices; owned networks and applications; and the communication layers that connect internal and external users to the Cloud and each other.
Migrate to Azure in 3 simple steps
 Feasibility Workshop
Feasibility Workshop
Customized to a client’s needs, this half-day interactive session is a unique opportunity for business and security leaders to understand their exposure and make informed decisions about moving to Azure.
 Readiness Assessment
Readiness Assessment
During this assessment, delivered both onsite and remotely, we access a client’s applications, people, processes, workflows, and current security technology, identifying and prioritizing key applications to migrate to the Cloud, as well as the processes and workflows that may need to be modified.
 Implementation & 24×7 Monitoring Services
Implementation & 24×7 Monitoring Services
Using the outcomes of the earlier steps, we implement a customized management and monitoring plan to meet specific business needs.
Talk to a Neovera Expert
Let’s discuss a solution that meets your business objectives and technical needs.